
In today's digital age, where data is as valuable as oil, protecting this crucial asset is essential for every organization. Threats arise from external sources like hackers and malware, as well as internal ones, including human errors and malicious insiders. This article will explore leading database security tools designed to shield your data from these varied risks.
- Networking - Tailscale
- Database credential management - Infisical
- On-demand database access - Indent
- All-in-one human-to-db operation - Bytebase
Tailscale
Tailscale is a VPN service that makes the devices and applications you own accessible anywhere in the world, securely and effortlessly. It enables encrypted point-to-point connections using the open source WireGuard® protocol, which means only devices on your private network can communicate with each other.
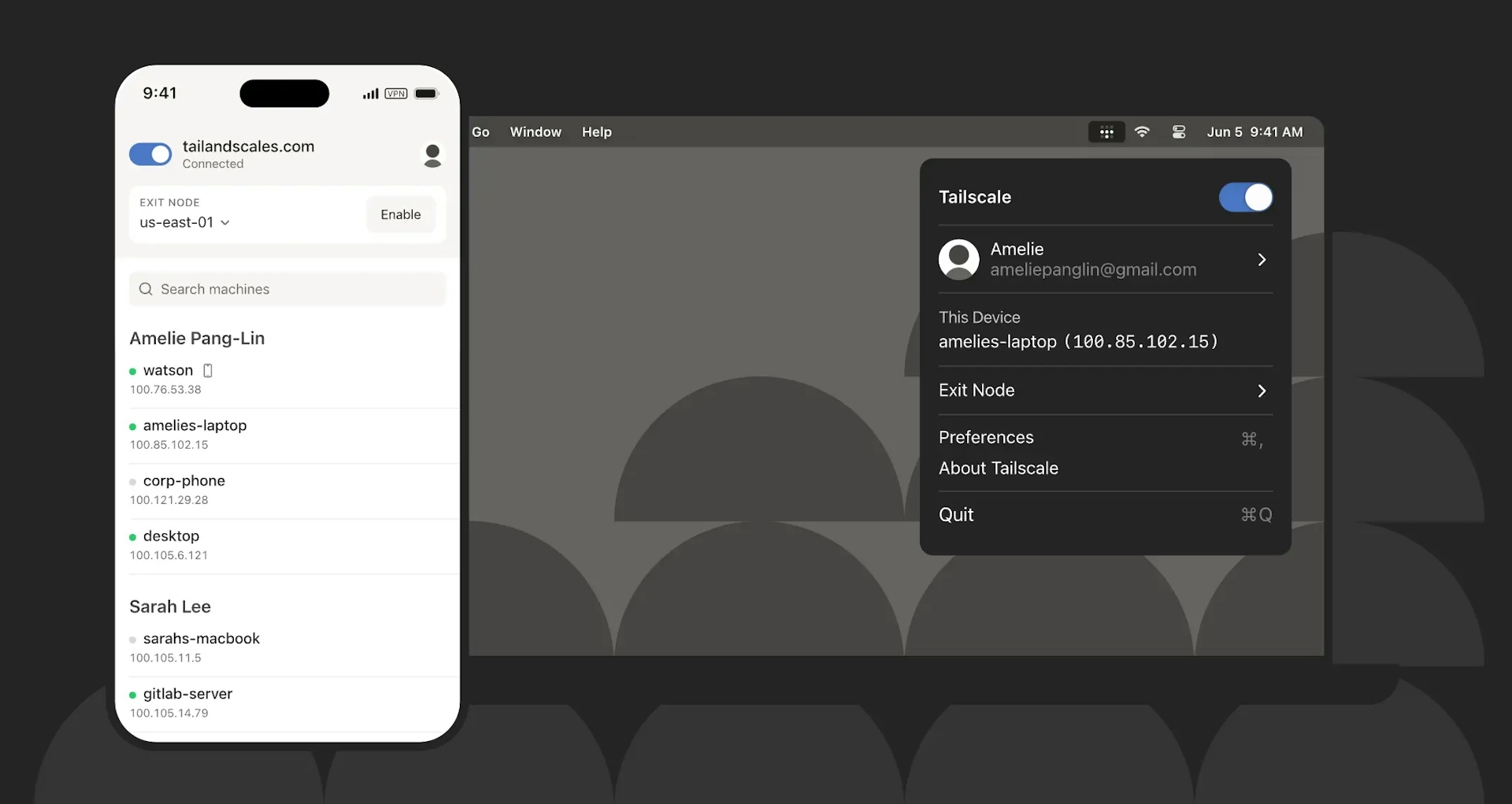
When it comes to databases, Tailscale can be used to connect to your database from any location globally, without having to expose your database to the public internet or setting up extra SSH tunnels.
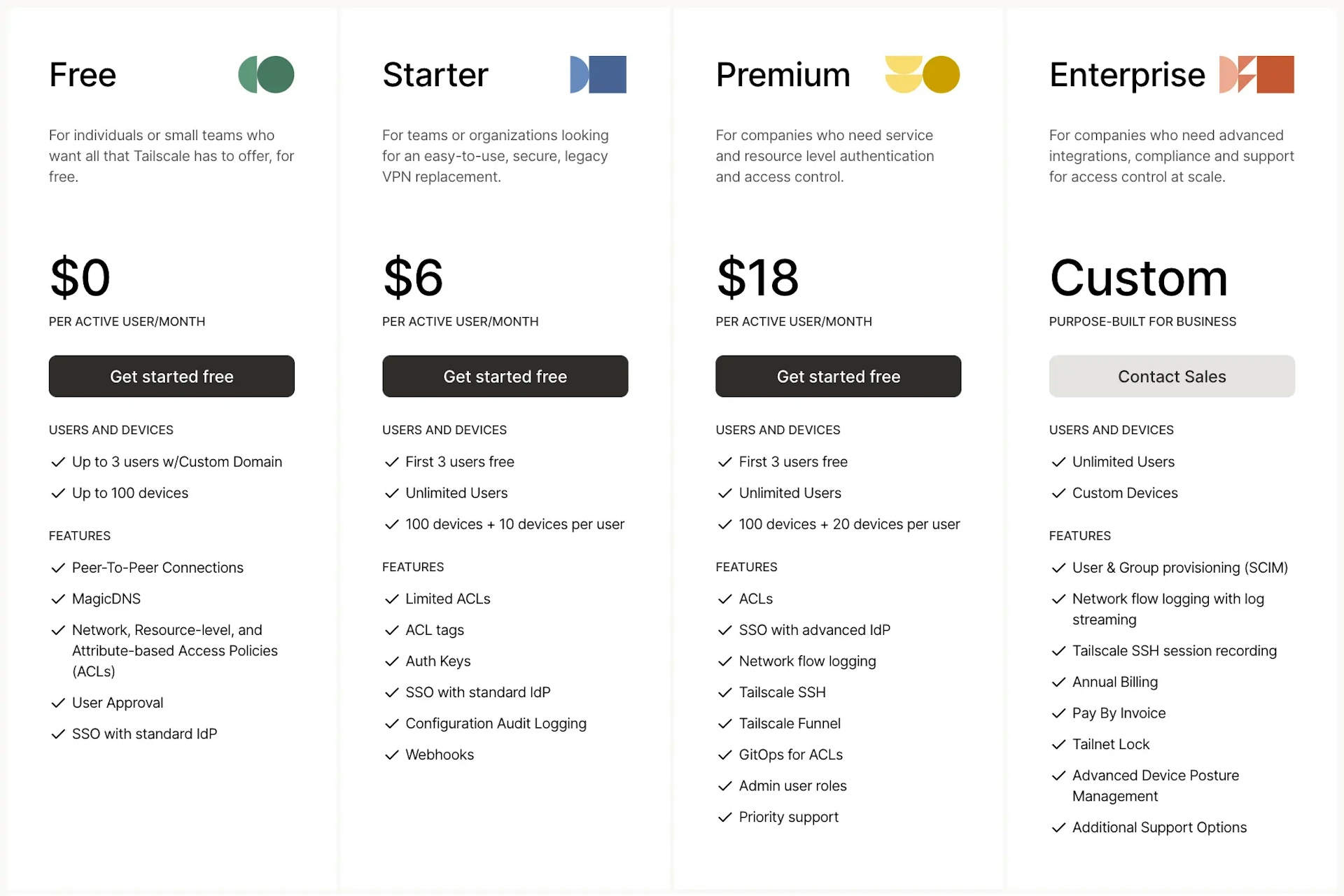
Its free tier accommodates up to 3 users and 100 devices, which is for individuals or small businesses. For additional capabilities like Access control and Audit logs, paid plans start at $6 per user per month.
Infisical
Infisical is an open-source, end-to-end encrypted secret management platform for storing, managing, and syncing application configuration and secrets like API keys, database credentials, and environment variables across applications and infrastructure. It is an alternative to HashiCorp Vault and AWS Secrets Manager.
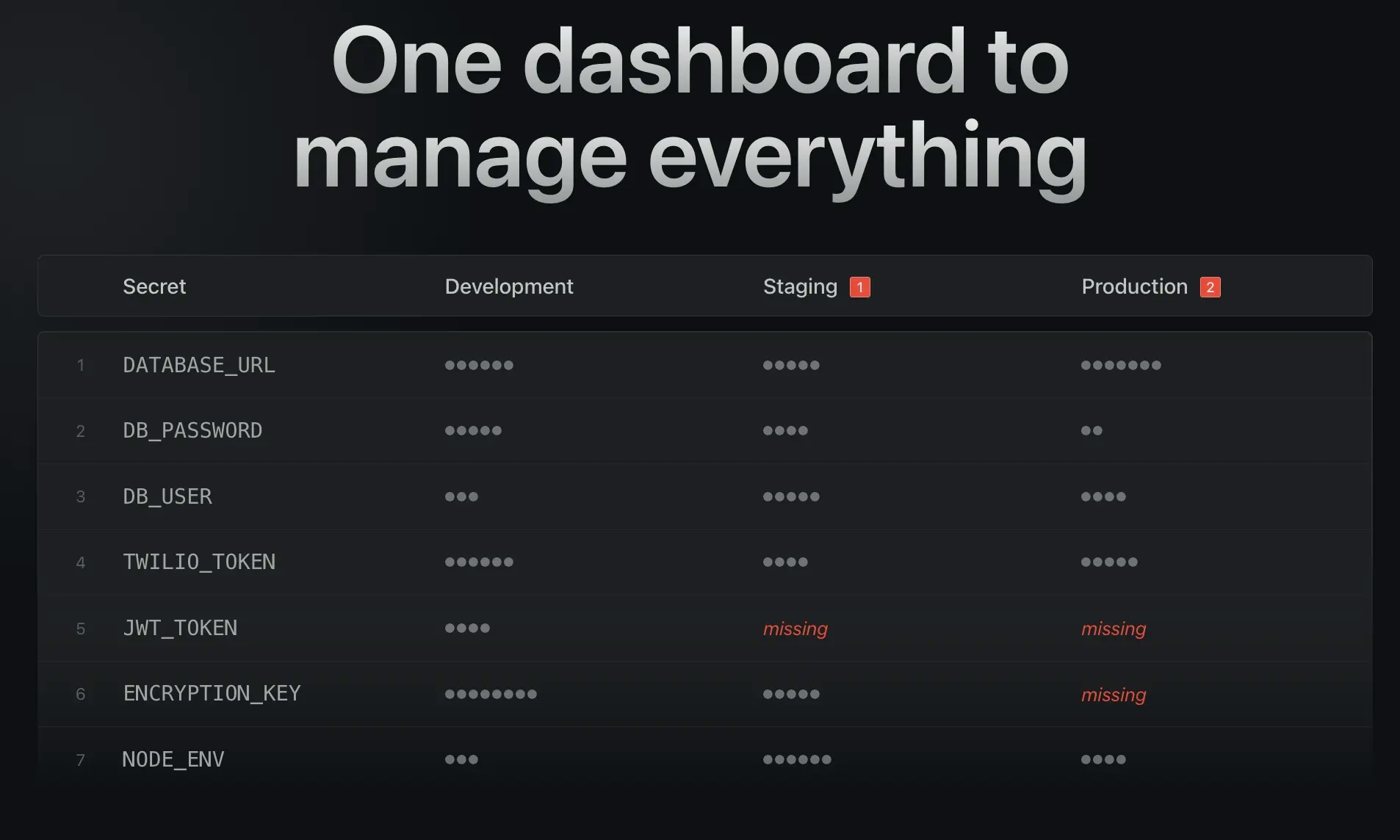
You have the option to host Infisical on your premises or utilize their cloud offering.
With its help, your database credentials can be stored in a secure vault and be accessed by your application only when needed. In this way, you can avoid storing your database credentials in your application code or configuration files. Access is facilitated through CLI, SDK, Docker, Kubernetes, or REST API.
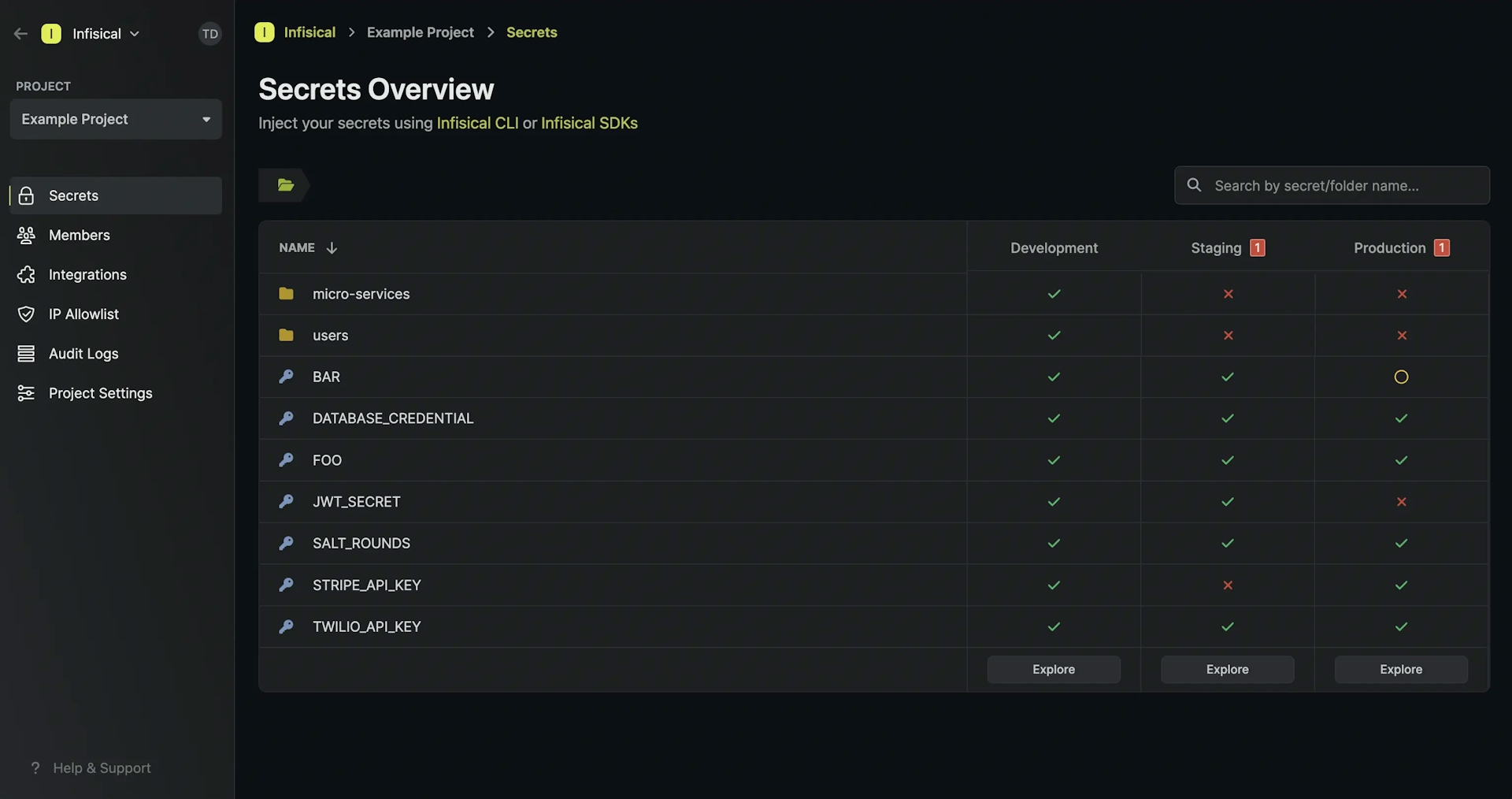
The free tier supports up to 5 developers and 3 environments, catering to hobbyists. For features such as Access Controls and Audit Logs, paid plans start at $6 per developer per month.
Indent
Indent provides team members with on-demand access to cloud apps and infrastructure in seconds. They aptly describe this innovation as the request access button for any software or service utilized by the company.
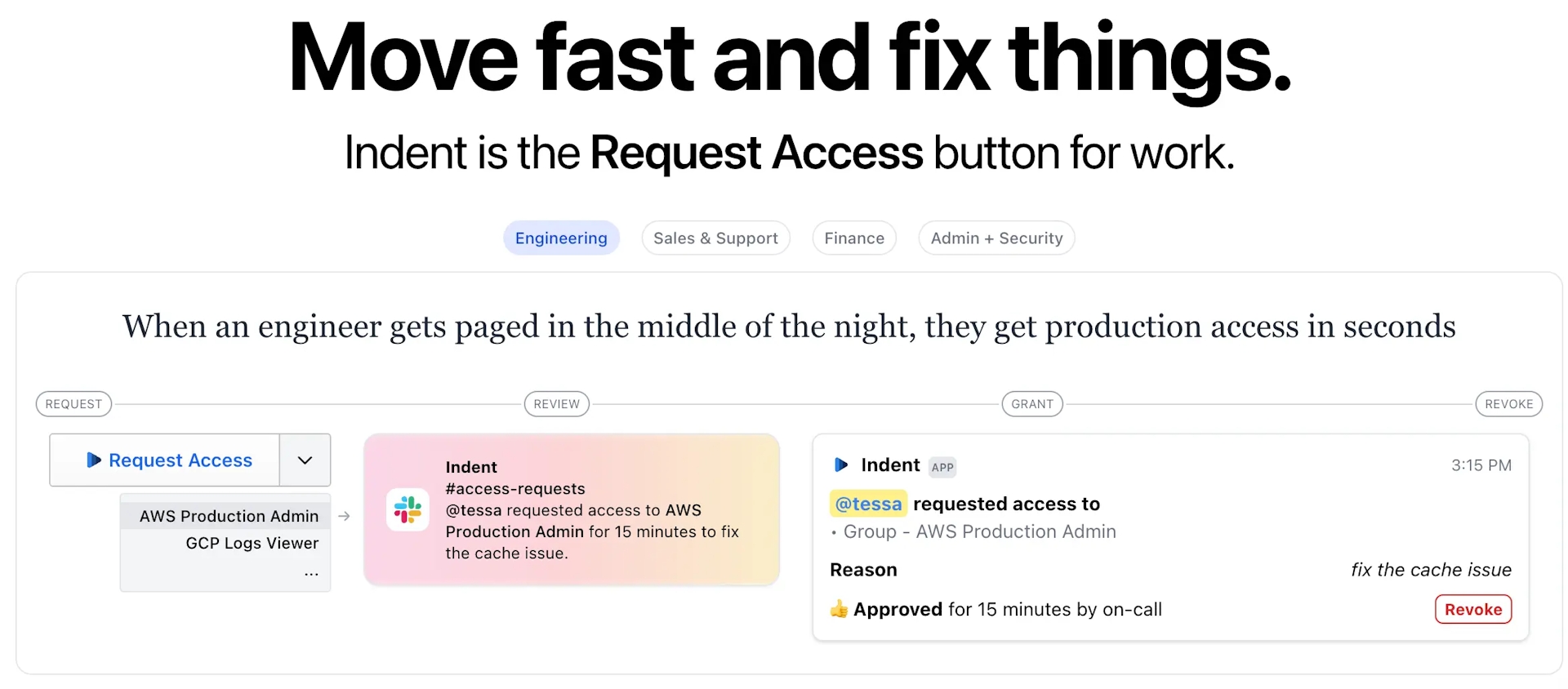
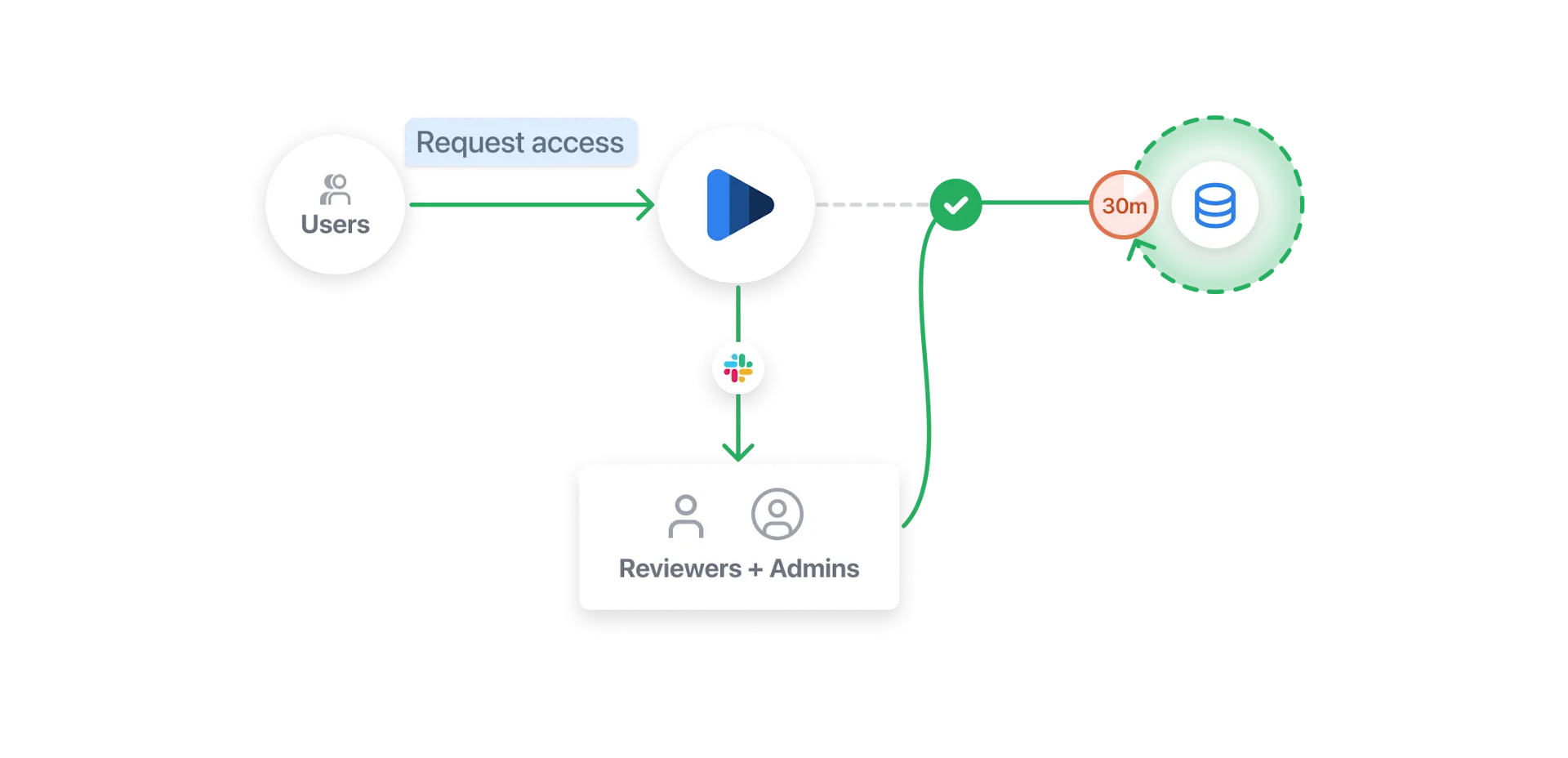
In the context of database access management, Indent provides you the capability to grant time-bound, granular access to systems that handle customer data. It offers three methods of integration:
- Zero Trust Network (ZTN) - e.g. Tailscale
- Identity Group - e.g. Okta
- Custom Integration
Indent provides a secure-by-default free tier suitable for small teams on a trial basis. For those requiring more, the paid plans begin at $8 per user per month.
Bytebase
Bytebase is an open-source database DevOps tool, it's the GitLab/GitHub for managing databases throughout the application development lifecycle. It offers a web-based collaboration workspace for DBAs, Developers and platform engineers. It consolidates disparate DB tools such as DBeaver, Liquibase, Flyway into a single place.
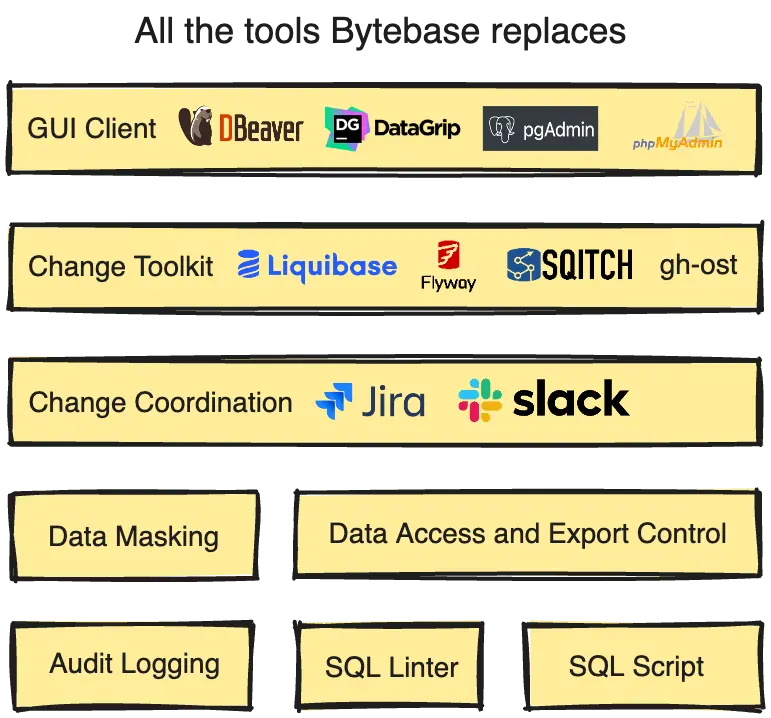
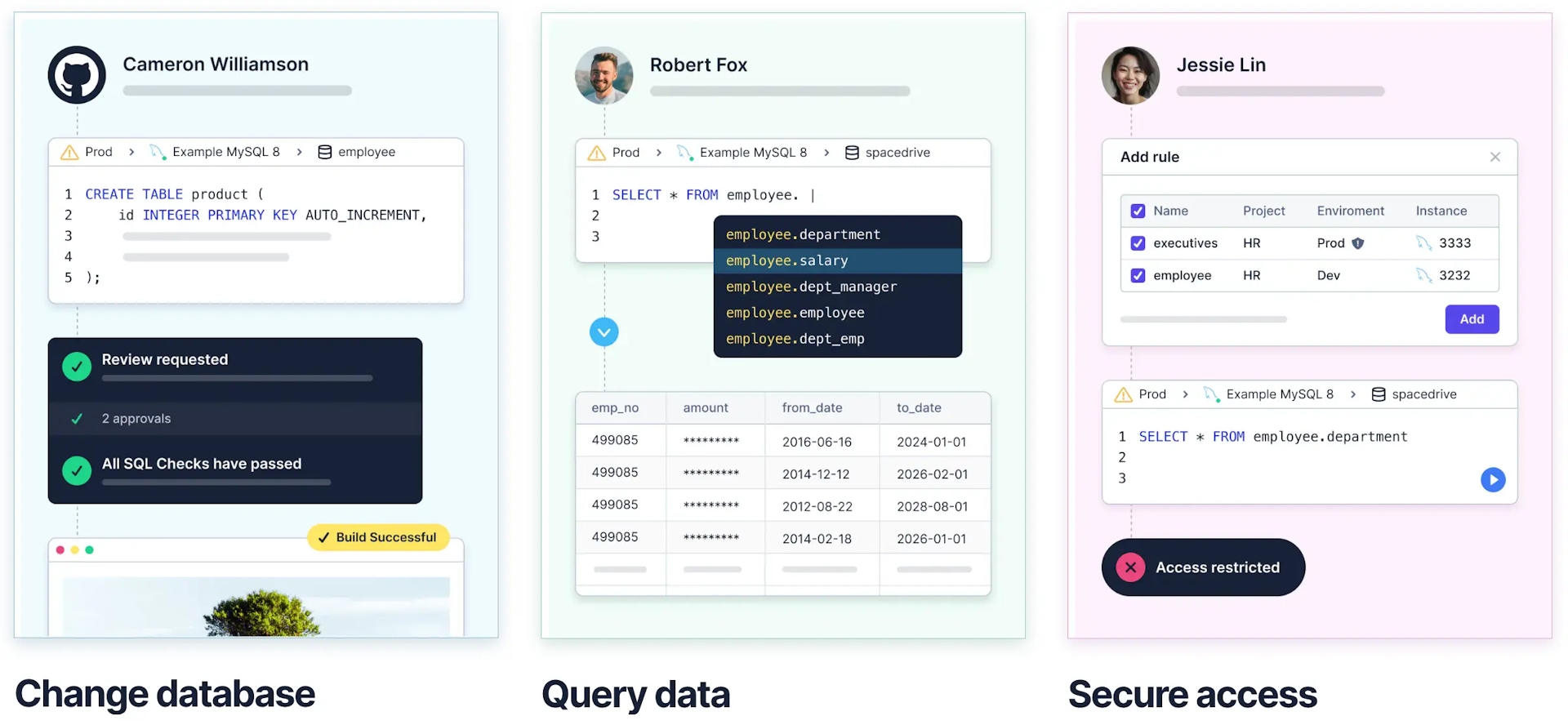
It seeks to encompass all interactions between humans and databases across every database, including managing changes, querying data, handling access, and beyond. Thanks to its features such as SQL Lint, Database CI/CD, Data Access Control, Data Masking, and more, you can be confident that all your database activities are executed via standardized procedures and completely auditable.
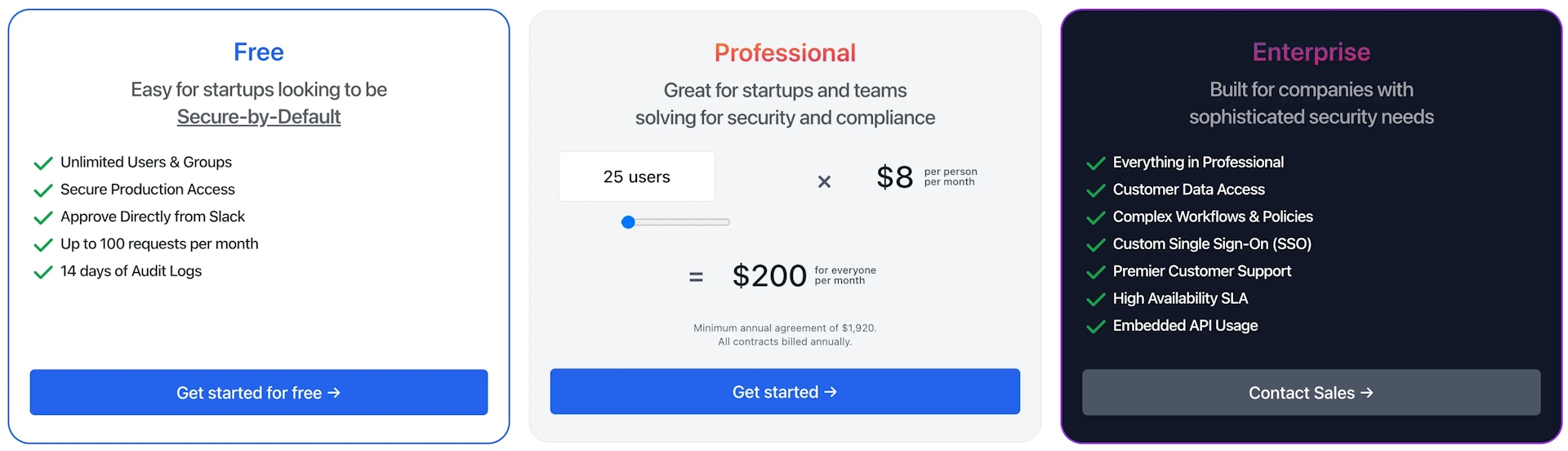
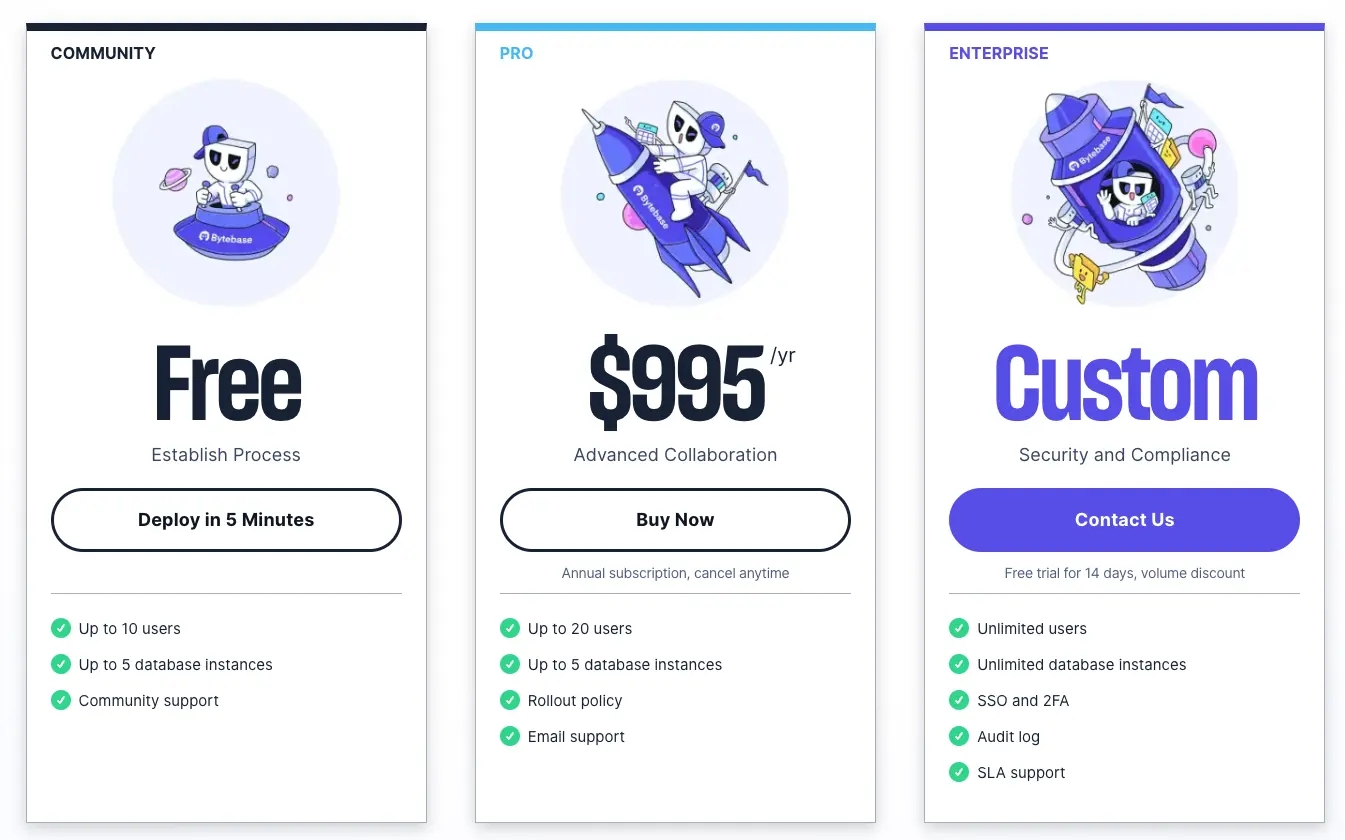
With Community Plan, you can have up to 10 users and up to 5 databases for free. For medium to large organizations, the Enterprise plan offers advanced options like Data Access Control, Audit Log, and additional features.
Summary
In this article, we have explored four database security tools that can help you protect your database from external and internal threats. Each tool offers its unique strengths; by understanding your specific needs, you can choose the one that most aligns with your requirements.




